Solar Plant Security - not an easy smash and grab
Designing and operating a security system for a solar plant sounds like a simple task. On closer inspection, solar developers and EPC’s find the task more challenging than first expected.
 Anybody who has considered the security options available on the market has asked themselves, “Do I install cameras with motion detection, microwave sensors, passive infrared sensors, or radar?” After all, any of these technologies will produce alarms, and many false alarms. Typically, too many alarms are generated, then the sensitivity is turned down to the point where the operator can get a good night’s sleep, but system does not function as designed.
Anybody who has considered the security options available on the market has asked themselves, “Do I install cameras with motion detection, microwave sensors, passive infrared sensors, or radar?” After all, any of these technologies will produce alarms, and many false alarms. Typically, too many alarms are generated, then the sensitivity is turned down to the point where the operator can get a good night’s sleep, but system does not function as designed.
Surveillance and intervention
Most of the video security industry is focused on recording video in high resolution and high frame rate on DVR/NVRs for playback after the damage is done. This approach is called, “surveillance.” Surveillance is adequate for retail operations or parking garages where the intruder is in close proximity to the camera, the area is always well lit, and the intruder is not wearing a mask or obscuring their face. Even in the best environment, the unlikely premise is that somebody will recognize the suspect and divulge his or her identity. In outdoor perimeter security applications like solar plant security, the operator needs to know if it is a person, not necessarily who the person is.
Protecting a solar plant has unique challenges that require protecting long, dark fence lines in remote areas with limited bandwidth and power. The solution is not about recording terabytes of high resolution video. The solution is alarming with video verification so an intervention can be deployed quickly to limit the amount of damage that can be done. Security is a local issue and local security guard firms are the best partners to contract for alarm intervention.
To secure a solar plant, alarms must be reduced to a manageable level and the cause of the alarm must be immediately known and verified. A motion sensor will create an alarm, but without a camera for verification, the alarm has no value. The traditional solution consists of a motion sensor system to generate the alarm, and a camera system for verification. Most intrusions happen at night along the perimeter so the maximum spacing between the camera poles is limited by the lighting strategy and capacity.
In an effort to reduce the pole and camera count, Pan, Tilt, Zoom (PTZ) cameras have been installed at some project sites with fence shaker sensor alarms. This works well at industrial sites that have unlimited bandwidth and the operator knows every inch of his property. However, in the case of a solar plant, 90% of the camera views are identical, and the operator can easily get lost. PTZ cameras are a good option for O&M applications such as checking the amount of dirt or snow on the modules, but are seriously lacking for solar plant security applications. The PTZ security strategy is intended to work like this; when the fence is moved, a sensor is triggered, and the PTZ camera looks to that area. Too often the camera turns and sees nothing. Was it a tumble weed slamming into the fence and disintegrating or was it a diversion for an intrusion outside the camera’s view? It can’t be known because the PTZ only sees what happened in the moments after the alarm, and does not explain what caused the alarm. In addition, the camera only sees what is illuminated in a spot light effect and the rest of the picture is black, which eliminates the only advantage of a PTZ camera.


Most intrusions happen at night so the perimeter must be illuminated to see what caused the alarm. If an operator installs perimeter lights that operate throughout the night they might also help the intruders find the way to the fence safely. Finally, without a robust internet connection, it will be nearly impossible to control the pan, tilt, and zoom function. The camera will stop reacting to commands, and then it will spin out of control when the connection is re-established.
Seeing heat, not light
Two military grade technologies have become available to the security mass market in recent years. The cost of thermal imaging cameras which see heat, not light, has dropped dramatically. With thermal imaging cameras there is no need for expensive, high-powered illumination of the perimeter. Illumination is no longer the limiting factor in pole spacing, now it is optics. Pole spacing can increase from around 200’ to 700’.
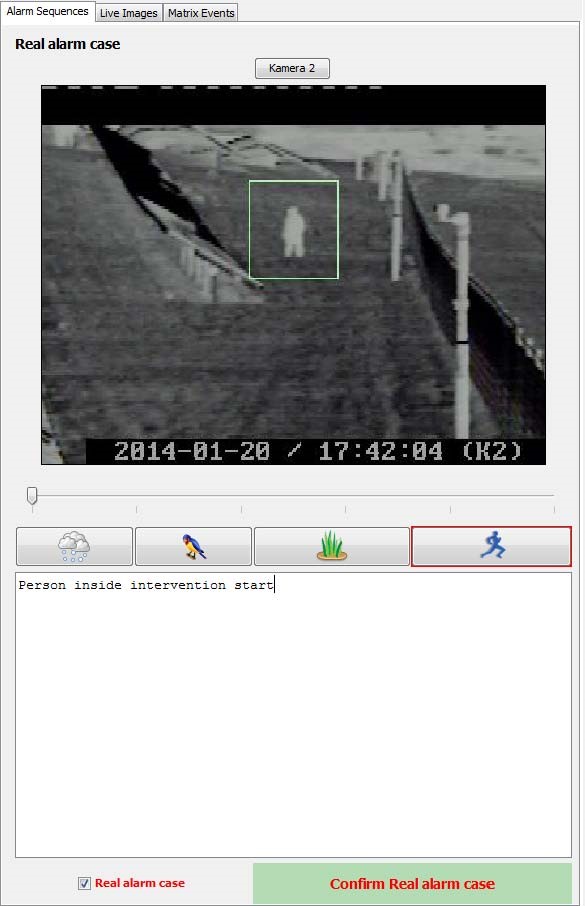
There is now video analytic algorithm software which analyzes live video, and distinguishes between people, moving vegetation, small animals, and weather events. Environmental movements are the primary cause of false alarms with motion detection and video analytic software filters out the false alarm movements. Video analytic software, combined with an alarm management software platform delivers alarms in the form of JPEG images including a detection box frame around what caused the alarm. This “Video Alarm System,” concept delivers the alarm and verification in small file sized jpeg image alarm sequences. The small file size is critical when a project is in a remote area and the only internet connection is via satellite. In the Video Alarm System concept, the alarm handler reviews pre-alarm, alarm and post-alarm images in alarm management software and immediately identifies what caused the alarm. A superimposed detection box frame (see image at left) in each image shows the guard exactly where to look, then he or she decides to deploy a response or clear the alarm from the queue where it will be compiled into a statistical report. In a case where the alarm is caused by a real intruder, the operator is presented with the unique intervention plan for this particular project site.
Placing thermal imaging cameras on poles around the perimeter in clockwise or counter-clockwise orientation allows each camera to secure the camera in front of it providing interlocking fields of view and eliminating any blind spots in the perimeter and protecting the cameras from sabotage. Since fixed cameras are used, the cameras are never looking in the wrong direction; one can see not only the alarm images, but also the pre-alarm images that show the moment before the alarm, which provides situational awareness.
Thermal imaging cameras are low-power consuming technology which can be powered with solar modules and batteries mounted on each pole. A substantial portion of the installation cost of a security system is the civil work. Solar powered camera poles and wireless radios that send the video to backhauls at select inverter skids for network access, eliminate the need for trenching and cabling.
Perimeter security at a glance
If a security vendor speaks about high resolution cameras and not illumination strategy, they have not thought through the challenges of solar plants. The optimum alarming method is video analytics with thermal imaging cameras. While Pan Tilt Zoom Cameras are not ideal for solar plant perimeter security, they are good for O&M applications. In perimeter security, Alarm Management Systems have security value, a Video Management System has no security value, but does have entertainment value. An ideal system would be designed for 100% perimeter coverage with fixed cameras. Going wireless will reduce the cost and complexity of cabling every pole to the nearest inverter skid. While no security system can eliminate all false alarms, an alarm management strategy will make the difference between responding to every tumbleweed or only the intruders.
A quick check to determine if the alarm concept works:
- Proper video detection: This can be checked by walking around the perimeter in a zig zag pattern from the perimeter fence to the inside of the service road.
- Illumination: Can the illumination blind the camera due to fog, rain, or insects like spiders? This will cause false alarms and is typical of integrated IR cameras.
- Sabotage at the pole: Can the cameras or lights be reached from outside the fence? What happens if the camera, light is covered, or the cable cut? Test this by unplugging the camera or light and cover the camera lens with cardboard.
- Intervention procedure: Is an appropriate intervention plan in place? Is the call-out working properly? Verify this by entering the site without disarming the system. Who will pay intervention fees due to false alarms?
Anson Moran is the chief executive officer at Viasys Solar Secure, Inc.
Viasys Solar Secure | www.viasys-iv.com
Volume: September/October 2015












